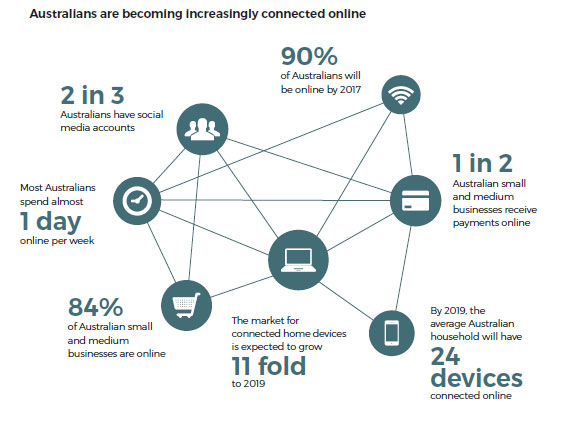
Reports of data breaches are an increasingly common occurrence. In recent weeks, Ticketmaster, HealthEngine, PageUp and the Tasmanian Electoral Commission have all reported breaches.
It is easy to tune out to what is happening, particularly if it’s not your fault it happened in the first place.
But there are simple steps you can take to minimise the risk of the problem progressing from “identity compromise” to “identity crime”.
In 2012 former FBI Director Robert Mueller famously said:
I am convinced that there are only two types of companies: those that have been hacked and those that will be. And even they are converging into one category: companies that have been hacked and will be hacked again.
The types of personal information compromised might include names, addresses, dates of birth, credit card numbers, email addresses, usernames and passwords.
In some cases, very sensitive details relating to health and sexuality can be stolen.
What’s the worst that can happen?
In most cases, offenders are looking to gain money. But it’s important to differentiate between identity compromise and identity misuse.
Identity compromise is when your personal details are stolen, but no further action is taken. Identity misuse is more serious. That’s when your personal details are not only breached but are then used to perpetrate fraud, theft or other crimes.
Offenders might withdraw money from your accounts, open up new lines of credit or purchase new services in your name, or port your telecommunication services to another carrier. In worst case scenarios, victims of identity crime might be accused of a crime perpetrated by someone else.
The Australian government estimates that 5% of Australians (approximately 970,000 people) will lose money each year through identity crime, costing at least $2.2 billion annually. And it’s not always reported, so that’s likely a conservative estimate.
While millions of people are exposed to identity compromise, far fewer will actually experience identity misuse.
But identity crime can be a devastating and traumatic event. Victims spend an average of 18 hours repairing the damage and seeking to restore their identity.
It can be very difficult and cumbersome for a person to prove that any actions taken were not of their own doing.
How will I know I’ve been hacked?
Many victims of identity misuse do not realise until they start to receive bills for credit cards or services they don’t recognise, or are denied credit for a loan.
The organisations who hold your data often don’t realise they have been compromised for days, weeks or even months.
And when hacks do happen, organisations don’t always tell you upfront. The introduction of mandatory data breach notification laws in Australia is a positive step toward making potential victims aware of a data compromise, giving them the power to take action to protect themselves.
What can I do to keep safe?
Most data breaches will not reveal your entire identity but rather expose partial details. However, motivated offenders can use these details to obtain further information.
These offenders view your personal information as a commodity that can be bought, sold and traded in for financial reward, so it makes sense to protect it in the same way you would your money.
Here are some precautionary measures you can take to reduce the risks:
- Always use strong and unique passwords. Many of us reuse passwords across multiple platforms, which means that when one is breached, offenders can access multiple accounts. Consider using a password manager.
- Set up two-factor authentication where possible on all of your accounts.
- Think about the information that you share and how it could be pieced together to form a holistic picture of you. For example, don’t use your mother’s maiden name as your personal security question if your entire family tree is available on a genealogy website.
And here’s what to do if you think you have been caught up in a data breach:
- Change passwords on any account that’s been hacked, and on any other account using the same password.
- Tell the relevant organisation what has happened. For example, if your credit card details have been compromised, you should contact your bank to cancel the card.
- Report any financial losses to the Australian Cybercrime Online Reporting Network.
- Check all your financial accounts and consider getting a copy of your credit report via Equifax, D&B or Experian. You can also put an alert on your name to prevent any future losses.
- Be alert to any phishing emails. Offenders use creative methods to trick you into handing over personal information that helps them build a fuller profile of you.
- If your email or social media accounts have been compromised, let your contacts know. They might also be targeted by an offender pretending to be you.
- You can access personalised support at iDcare, the national support centre for identity crime in Australia and New Zealand.
The vast number of data breaches happening in the world makes it easy to tune them out. But it is important to acknowledge the reality of identity compromise. That’s not to say you need to swear off social media and never fill out an online form. Being aware of the risks and how to best to reduce them is an important step toward protecting yourself.
For further information about identity crime you can consult ACORN, Scamwatch, or the Office of the Australian Information Commissioner.
If you are experiencing any distress as a result of identity crime, please contact Lifeline.
Author: Cassandra Cross Senior Lecturer in Criminology, Queensland University of Technology